Red Teaming
Will your organization be able to detect and stop real cyber-attacks in time, before it is too late?
When was the last time you tested the physical, technical and process-based security mechanisms you rely on to defend your and your customer’s data?
Red Teaming is a full-scope, multi-layered attack simulation designed to measure how well your people, networks, applications, and physical security controls can withstand an attack from a motivated real-life adversary.
Our Red Team engagement covers:
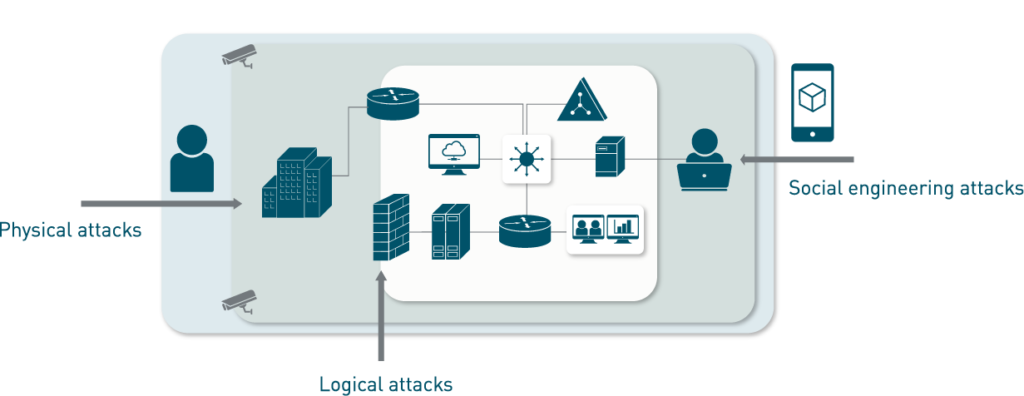
- Technology & Information Security — Networks, applications, routers, switches, appliances, sensitive data, phishing, etc.
- People — Staff, independent contractors, departments, business partners, etc.
- Physical — Offices, warehouses, substations, data centers, buildings, etc.
The purpose of conducting a Red Team assessment is to demonstrate how real-world attackers can combine several vulnerabilities from different areas to achieve their goals, and to help you take a defense-in-depth approach while continuously improving the security of your people, processes, and technology.
Red Teaming will help you:
- Assess the organization’s ability to detect, respond and prevent sophisticated and targeted threats
- Prioritize remediation plans based on what is causing the greatest risk
- Build a business case for improvements, deploying new solutions, and other security spending
Our Red Teaming Methodology:
- Planning
- Reconnaissance
- Preparation
- Weaponization
- Exploitation
- Lateral movement and foothold
- Escalation
- Exfiltration
The process:
- You contact us and let us know you are interested
- We will set up a meeting to discuss your needs, desired goals and scope
- Our Red Teaming experts will develop a plan with multiple attack scenarios to reach the goals – detailing methods and tools
- Suggested Rules of Engagement for the whole exercise
- Suggested dates
- We will call for a plan review in which you get to see the plan and suggest changes
- You will get some time to go over the plan at your own pace
- You agree to the plan (with possible changes)
- The Read Team operators start with their work
What you get:
- To experience the progression of a realistic cyber-physical attack from a motivated adversary.
- Practice for your SOC/NOC/cyber security
- A test of your incident response methodology and processes
- An extensive report detailing:
- The full attack story – what happened, where and when – what was the outcome. What did the Red Team operators do, how they interacted with your systems and staff
- All found and utilized vulnerabilities by the Red Team operators
- Recommendations on how to prevent and/or mitigate the found and utilized vulnerabilities
- A short movie with the edited body camera footage from the Red Team operators
- The results from the reconnaissance phase
Contact us today!